In their recent version of macOS, named “Catalina” (10.15), Apple introduced a feature protecting users from executing malicious software downloaded from the Internet. To separate “good” from “bad” software, Apple implemented a so called “notarization” process, and software which has not been “notarized” cannot be executed on macOS Catalina without further ado.
Unfortunately, Apple tightened the criterias for notarization by February 2020 and excludes within others all software from notarization which build upon Java 8 – this also affects QF-Test in the latest version 5.0. Therefor, after downloading and moving QF-Test to the application folder, another step is required to execute QF-Test on those systems:
After starting QF-Test a message is shown that Apple cannot check QF-Test for malicious software:
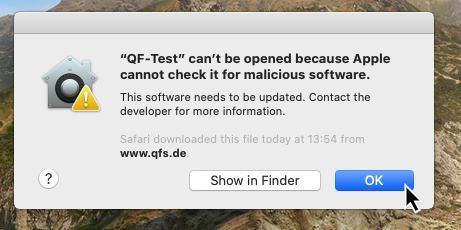
Close the dialog by clicking “OK”.
Then open the system preferences and there the section “Security & Privacy”:

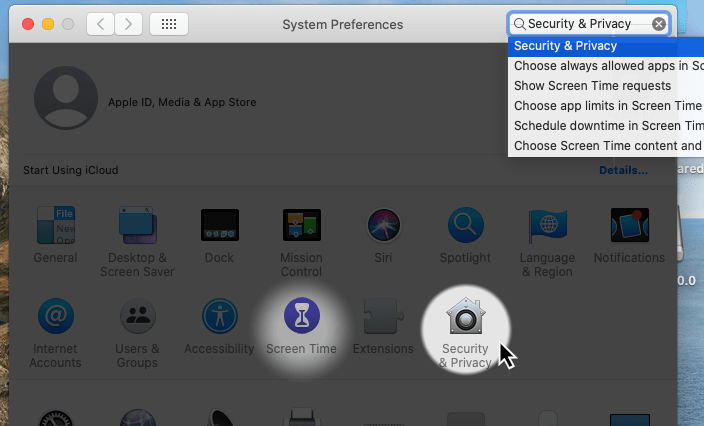
In the tab “General” you can now find the remark that the start of QF-Test has been blocked.
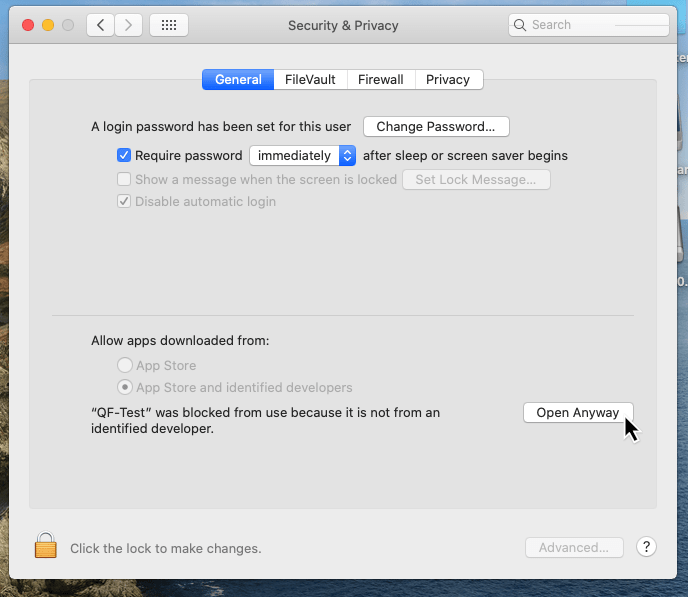
Confirm the execution of QF-Test by clicking “Open Anyway”. In the following dialog, you can finally allow the execution of QF-Test:

Now you can use QF-Test like usual, the operating system remembers the exception.